North Korean state hackers have exploited a zero-day, remote code execution vulnerability in Google Chrome web browser for more than a month before a patch became available, in attacks targeting news media, IT companies, cryptocurrency, and fintech organizations.
Google’s Threat Analysis Group (TAG) attributed two campaigns exploiting the recently patched CVE-2022-0609 (described only as “use after free in Animation” at the moment) to two separate attacker groups backed by the North Korean government.
Exploit actively deployed since early January
In a report shared in advance with BleepingComputer, Google TAG details the tactics, techniques, and procedures (TTPs) related to these activities, which targeted more than 330 individuals.
The victims were targeted via emails, fake websites, or compromised legitimate websites that would ultimately activate the exploit kit for CVE-2022-0609.
Google TAG discovered the campaigns on February 10 and addressed the vulnerability in an emergency Google Chrome update four days later.
However, the researchers say that the earliest sign of the zero-day vulnerability being actively exploited were found on January 4, 2022.
The connection with the North Korean hackers, also referred to as the Lazarus Group, is given by one of the campaigns, which has direct infrastructure overlap with another activity attributed to the same threat actor last year: targeting security researchers using fake Twitter and LinkedIn social media accounts.
Breaching legit sites to serve the exploit
One of the two North Korean threat subgroups focused on more than “250 individuals working for 10 different news media, domain registrars, web hosting providers and software vendors.”
Google TAG notes that this activity is consistent with Operation Dream Job, a North Korean cyberespionage campaign detailed by researchers at ClearSky in August 2020.
Operation Dream Job lured victims with fake job offers from prominent defense and aerospace companies in the U.S., among the names being Boeing, McDonnell Douglas, and BAE.
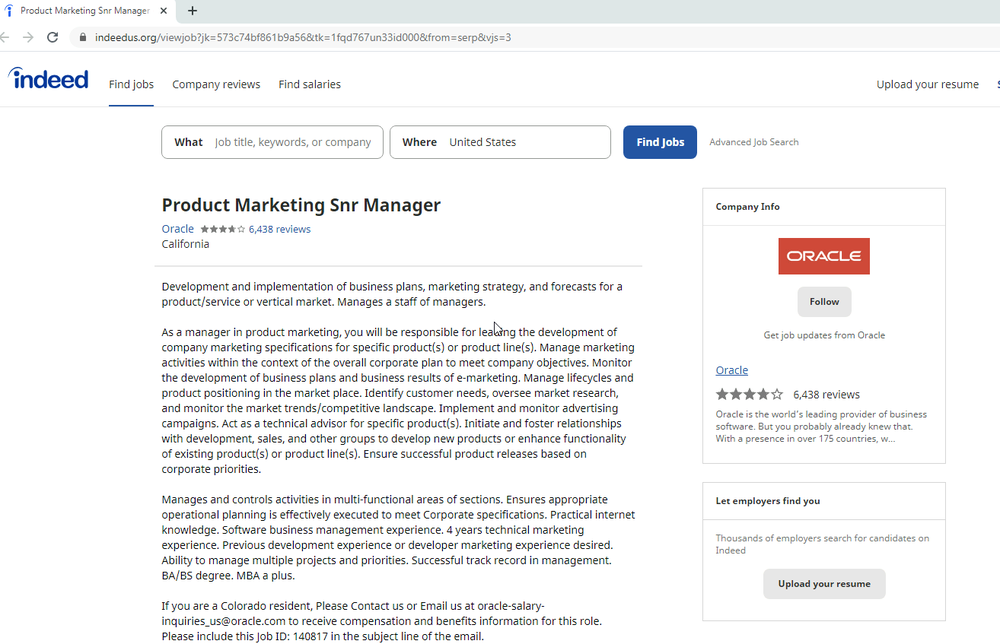
Google TAG notes that in the campaign it discovered the targets received phishing emails with fake job opportunities from recruiters at Disney, Google, and Oracle.
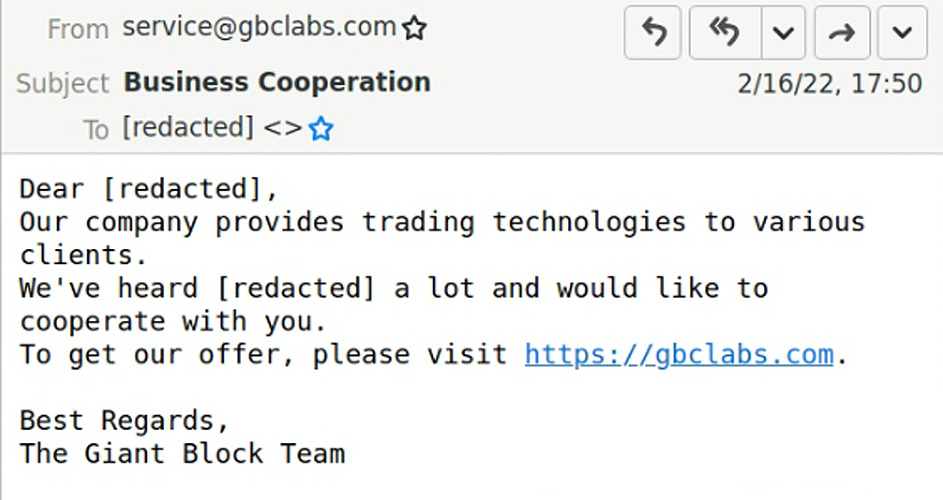
“The emails contained links spoofing legitimate job hunting websites like Indeed and ZipRecruiter,” the researchers explain, adding that clicking on them would serve victims a hidden iframe that triggered the exploit kit.
For this campaign, the attacker registered some domains, such as disneycareers[.]net and find-dreamjob[.]com, but also compromised at least one legitimate website.
The second campaign discovered by Google TAG to use the same exploit kit for CVE-2022-0609 targeted more than 85 users in cryptocurrency and fintech industries and is attributed to the same group behind Operation AppleJeus [1, 2, 3], detailed by Kaspersky in 2018.
“This included compromising at least two legitimate fintech company websites and hosting hidden iframes to serve the exploit kit to visitors. In other cases, we observed fake websites - already set up to distribute trojanized cryptocurrency applications - hosting iframes and pointing their visitors to the exploit kit” - Google TAG
Just like with the previous campaign, this group also registered new domains and compromised a couple of legitimate ones.
Protecting the exploit chain
Analyzing the exploit, the researchers found that the attacker had integrated several protection features that made it more difficult to recover the multiple exploit stages needed to compromise the targets.
For instance, the iframe with the link to the exploit kit was served at specific times, some targets received unique IDs (to serve the exploit only once), each stage of the kit was encrypted (client responses, too), and moving to secondary stages would depend on the success of the previous one.
The researchers say that the initial activity of the kit was to fingerprint the target system by collecting details like user-agent and screen resolution.
If this data matched a set of specific requirements (unknown at this time), the client received a Chrome remote code execution (RCE) and Javascript code that requested a sandbox escape, to move out the confinements of the web browser, onto the system.
Google TAG could not recover any of the stages that followed the initial remote code execution step, though.
The researchers found evidence that the North Korean hackers were not interested in Google Chrome users only and they also checked users of Safari on macOS and Firefox, directing them “to specific links on known exploitation servers.”
At the time of the analysis, though, the observed URLs did not return any response.
A complete list of indicators of compromise, including exploitation URLs and attacker-registered domains, is available in Google TAG's report.

.jpg)
Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now