
Verizon warned an undisclosed number of prepaid customers that attackers gained access to Verizon accounts and used exposed credit card info in SIM swapping attacks.
"We determined that between October 6 and October 10, 2022, a third party actor accessed the last four digits of the credit card used to make automatic payments on your account," Verizon said in an alert published this week.
"Using the last four digits of that credit card, the third party was able to gain access to your Verizon account and may have processed an unauthorized SIM card change on the prepaid line that received the SMS linking to this notice. If a SIM card change occurred, Verizon has reversed it."
Verizon added that it blocked further unauthorized access to its clients' accounts and found no evidence that this malicious activity is still ongoing.
The company also reset the Account Security Codes (PINs) for an undisclosed number of customers "in an abundance of caution."
According to the notification, the attackers couldn't access the full credit card number or the customers' banking information, financial information, passwords, Social Security numbers, tax IDs, or other personal details since user accounts don't contain this info.
However, Verizon said the threat actors could have accessed names, telephone numbers, billing addresses, price plans, and other service-related information on compromised accounts.
SIM swap attack used to steal crypto
One of the Verizon customers who received this notice told BleepingComputer that they were the victims of a SIM swap attack more than a week before Verizon alerted customers.
"On 10/7 when I was sim-swapped, the attackers breached my email and attempted to access my crypto accounts," they told BleepingComputer.
"I suspect they used information from the Coinbase breach to target me but got access due to the exposure of credit card info from Verizon."
SIM swapping (aka SIM hijacking, SIM splitting, or SIM jacking) allows criminals to take control of a target's phone number by convincing their mobile carriers to swap the phone number to an attacker-controlled SIM card using social engineering or with the help of bribed employees.
While Verizon's notification was published on its website earlier this week to warn customers of these attacks, the telecom giant made sure that search engines won't index the page by adding 'noindex' and 'nofollow' tags to its metadata.
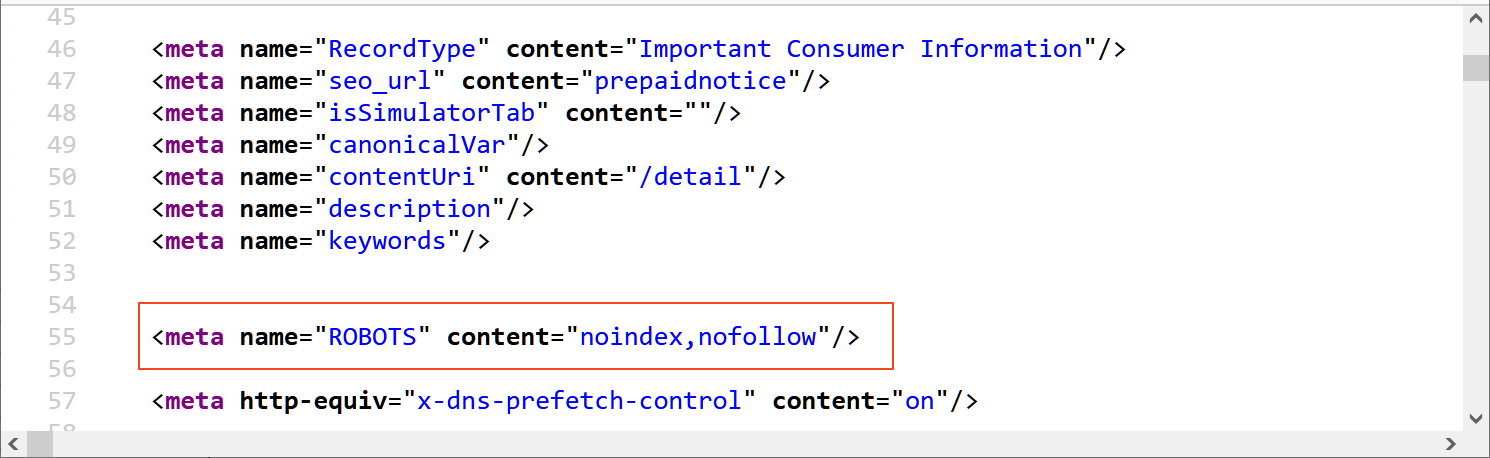
"We recently identified possible unauthorized activity involving about 250 prepaid wireless accounts. We secured these accounts and put in place additional measures to protect our customers from further unauthorized access or fraud," a Verizon spokesperson told BleepingComputer.
"Verizon has notified the impacted customers and advised on additional steps the customers can take to enhance their account security. We take these matters seriously, and continually enhance and evolve our security protocols to keep customer data and accounts secure.
"As always, if any customer believes their account was accessed without authorization, they should reach out to us online, in the MyVerizon app, or by calling 888-483-7200."
Customers are advised to set a new Verizon PIN code to secure their Verizon account from future attacks, as well as a new password and secret question to safeguard their My Verizon online accounts.
Verizon also allows customers to defend against SIM swapping attacks by enabling the free 'Number Lock' protection feature through the My Verizon app or the My Verizon website.
Once the phone number is locked, it can no longer be ported to another line/carrier or swapped to another SIM unless the account owner removes the lock.
One year ago, Verizon-owned digital wireless carrier Visible also admitted that some customer accounts were hacked following several days of technical problems.
Update October 18, 16:28 EDT: Added Verizon statement.


Comments
patboy08 - 1 year ago
I wasn't affected but I changed all my info anyway. Not surprising the attackers went for prepaid accounts since they are not able to use the Number Lock feature. I wanted to enable it on my account but I assume its a postpaid only feature.
johnlsenchak - 1 year ago
What Verizon Wireless is not telling you is that they have done absolutely nothing to stop the robo-calling from India which is allowing fraud to occur on a daily basis