
The Costa Rican President Rodrigo Chaves has declared a national emergency following cyber attacks from Conti ransomware group on multiple government bodies.
BleepingComputer also observed Conti published most of the 672 GB dump that appears to contain data belonging to the Costa Rican government agencies.
The declaration was signed into law by Chaves on Sunday, May 8th, same day as the economist and former Minister of Finance effectively became the country's 49th and current president.
Costa Rica under national emergency after cyberattacks
On Sunday, May 8th, the newly elected Costa Rican President Chaves declared a national emergency citing ongoing Conti ransomware attacks as the reason.
Conti ransomware had originally claimed the ransomware attack against Costa Rican government entities last month.
The country's public health agency Costa Rican Social Security Fund (CCSS) had earlier stated that "a perimeter security review is being carried out on the Conti Ransomware, to verify and prevent possible attacks at the CCSS level."
En este momento se realiza revisión en la seguridad perimetral sobre el Ransomware Conti, para verificar y prevenir posibles ataques a nivel de la CCSS.
— CCSSdeCostaRica (@CCSSdeCostaRica) April 19, 2022
BleepingComputer observed that as of yesterday Conti's data leak site had been updated to state that the group had leaked 97% of the 672 GB data dump allegedly containing information stolen from government agencies:
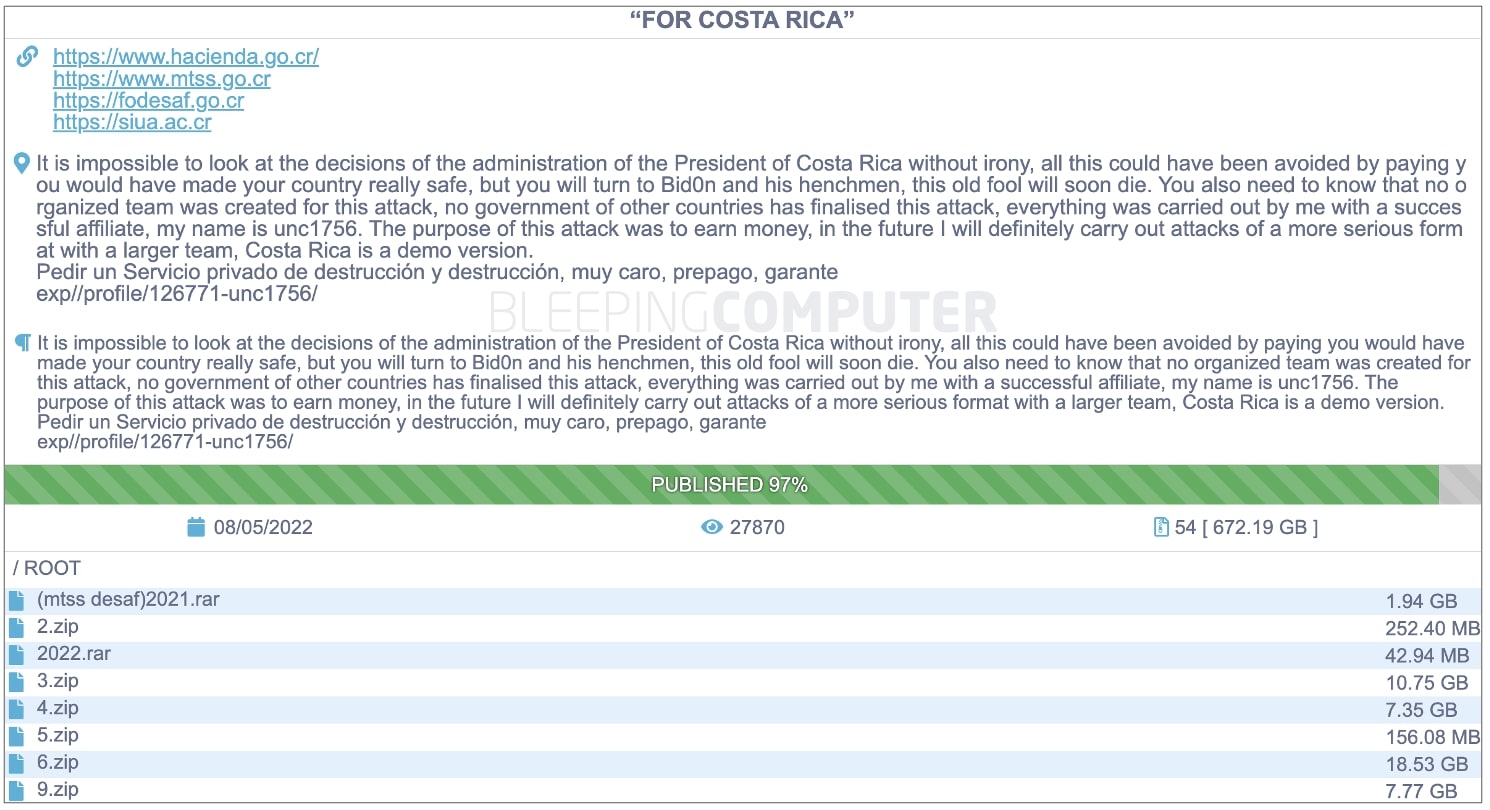
The public body that first suffered damage from Conti's cyberattack is the Ministry of Finance which still has not yet fully evaluated the scope of the security incident or to what extent has taxpayers' information, payments, and customs systems have been impacted.
Conti earlier demanded a $10 million ransom from the Ministry which the government declined to pay, according to Swissinfo.ch.
Conti's leak site presently lists the following government purportedly affected by the attack, as seen by BleepingComputer:
- The Costa Rican Finance Minsitry, Ministerio de Hacienda
- The Ministry of Labor and Social Security, MTSS
- The Social Development and Family Allowances Fund, FODESAF
- The Interuniversity Headquarters of Alajuela, SIUA
BleepingComputer has not yet analyzed the leaked data but a preliminary analysis of a very small subset of the leaked data shows source code and SQL databases that appears to be from government websites.
Rather than attributing this cyberattack to nation-state hackers, Conti threat actor "UNC1756," along with their affiliate, has solely claimed responsibility for it. The threat actor has threatened to conduct future attacks of "a more serious form."
News outlet Amelia Rueda that earlier reported on the development states the execute decree No. 42542 from the President establishes an emergency:
"The attack that Costa Rica is suffering from cybercriminals, cyberterrorists is declared a national emergency and we are signing this decree, precisely, to declare a state of national emergency in the entire public sector of the Costa Rican State and allow our society to respond to these attacks as criminal acts," said the President, accompanied by Minister of the Presidency, Natalia Díaz, and the Minister of Science, Innovation, Technology and Telecommunications (Micitt), Carlos Alvarado.
Since April 18th, the Treasury's digital services have been unavailable which is affecting the entire "productive sector" due to government procedures, signatures, and stamps having been disrupted, reports, Amelia Rueda.
"We signed the decree so that the country can defend itself from the criminal attack that cybercriminals are making us. That is an attack on the Homeland and we signed the decree to have a better way of defending ourselves," added President Chaves.
Other agencies to have been impacted by Conti's attacks include:
- Administrative Board of the Electrical Service of the province of Cartago (Jasec)
- The Ministry of Science, Innovation, Technology, and Telecommunications
- National Meteorological Institute (IMN)
- Radiographic Costarricense (Racsa)
- Costa Rican Social Security Fund (CCSS).
As reported by BleepingComputer last week, the U.S. government is rewarding up to $15 million to anyone providing information that can lead to the identification and arrests of Conti ransomware's leadership and operators.
The U.S. Department of State pledged to offer up to $10 million for information on the identity and location of the threat actors with an additional $5 million bounty for leading to the arrest and/or convictions of the individuals responsible for these attacks.
Conti ransomware group in review
Conti is a Ransomware-as-a-Service (RaaS) operation linked to the Russian-speaking Wizard Spider cybercrime group (also known for other notorious malware, including Ryuk, TrickBot, and BazarLoader).
The cybercrime gang's victims include Ireland's Health Service Executive (HSE) and its Department of Health (DoH), asking the former to pay a $20 million ransom.
The FBI also warned in May 2021 that Conti operators tried to breach over a dozen US healthcare and first responder organizations.
In August 2021, a disgruntled affiliate leaked Conti's training materials, including info on one of its operators, a manual on deploying various malicious tools, and numerous help documents allegedly provided to the group's affiliates.
According to analysts from multiple cybersecurity firms, Conti is now managing various side businesses meant to sustain its ransomware operations or pay for initial network access when needed.
One such side operation is the recently emerged Karakurt data extortion group, active since at least June 2021 and recently linked to Conti by researchers from Advanced Intelligence, Infinitum, Arctic Wolf, Northwave, and Chainalysis, as the cybercrime gang's data extortion arm.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now