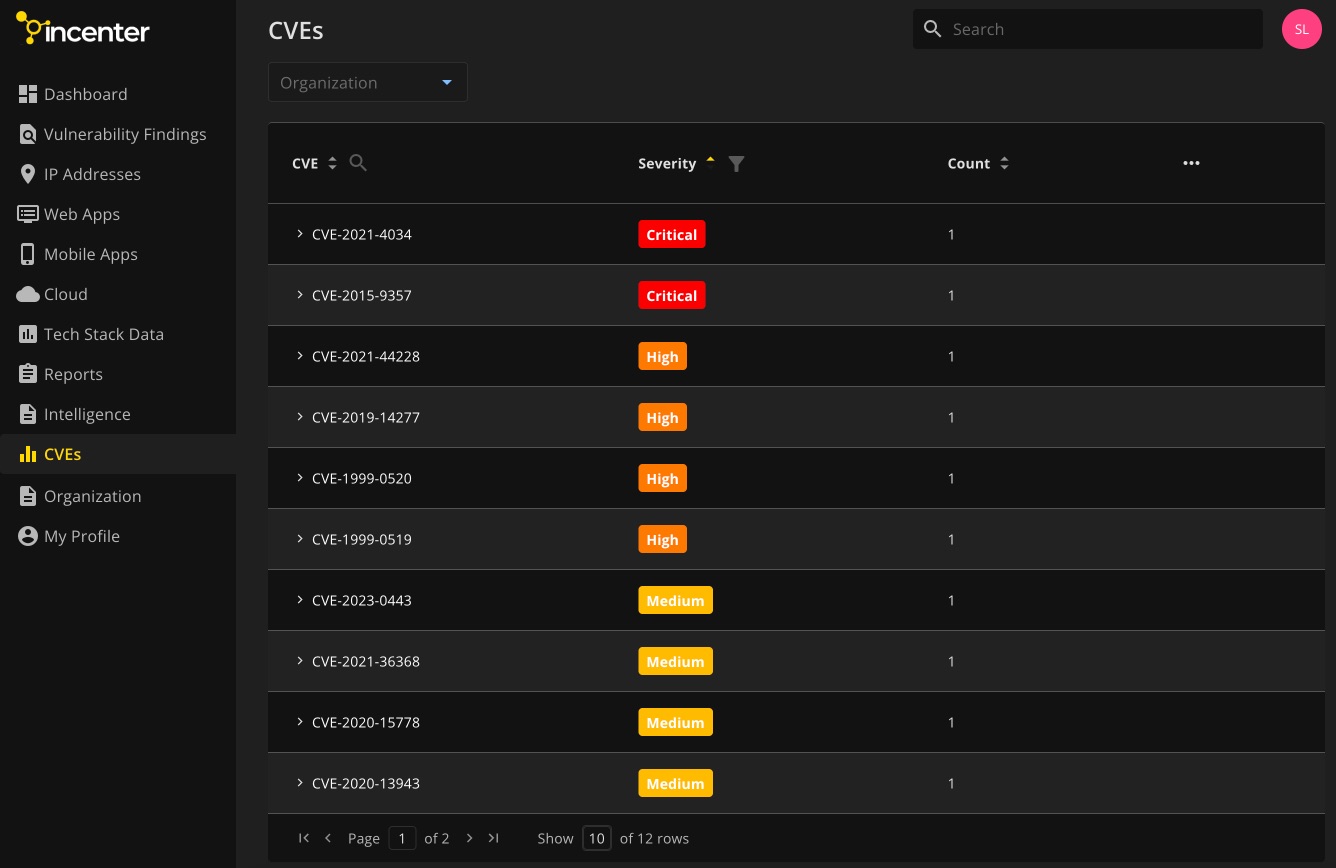
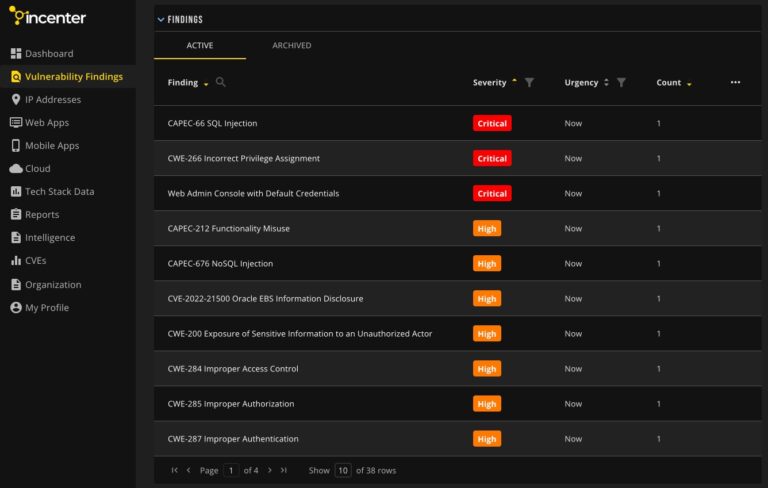
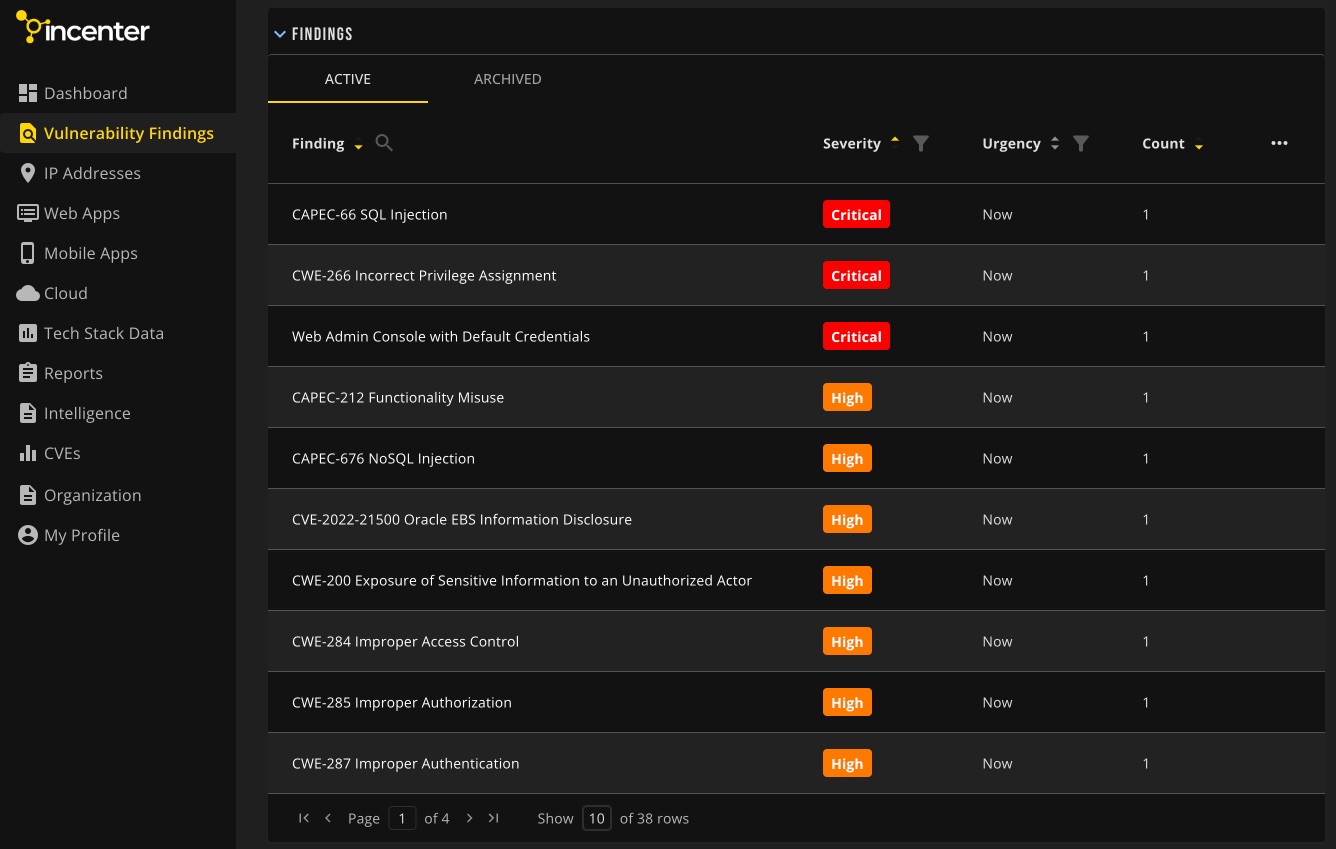
Incenter
- 24/7/365 cybersecurity protection
- Saves an average of 20% on cybersecurity budgets
- Reduces remediation timelines by over 38%
- Automation with human expertise
- Consolidates multiple cybersecurity tools into a single solution
Incenter provides industry leading automated penetration testing that protects organizations, prevents breaches, and ensures compliance.
Click a button below to see how Incenter can benefit your organization.
See what Incenter can do for your business:


Reduce your incident response costs
The average cost of a cybersecurity data breach in the United States is $9.44 million1 and takes an average of 287 days to identify and contain.2
Incenter proactively identifies and detects vulnerabilities, preventing an incident before it occurs, minimizing both the chance of a security breach and the direct costs associated with it.
Read more about how Incenter can reduce your costs
1 & 2 IBM Security, Ponemon Institute. (2022). Cost of a Data Breach Report 2022. https://www.ibm.com/downloads/cas/3R8N1DZJ

Capitalize on the most of your security investment
The average enterprise utilizes 45 cybersecurity tools or technologies.3 Incenter can consolidate offensive security tools to a single platform. By deploying Incenter, you optimize your investment with one solution to identify and prioritize vulnerabilities, manage inventory, and improve risk mitigation and resource allocation.
Find out how Incenter can give you more value
3 IBM Security, Ponemon Institute. (2020). The 2020 Cyber Resilient Organization Study by the Ponemon Institute. https://newsroom.ibm.com/2020-06-30-IBM-Study-SecurityResponse-Planning-on-the-Rise-But-Containing-Attacks-Remains-an-Issue
Protect your brand's reputation
In the digital age, a single security breach can irrevocably damage your organization’s brand, with roughly 70% of consumers saying they would halt further commerce with a company due to a data breach.4 The damage to an organization can be overwhelming and produce long-lasting impacts.
While exhaustive efforts are placed into the generation of a strong brand, the same energy should be applied to protecting it.
Incenter helps protect your brand reputation against the risk that could cause it irreparable harm.
Find out how Incenter can protect your brand
4 Thales Group (study conducted when it was still Gemalto). (2017). Breach Level Index (BLI). https://www6.thalesgroup.com/breach-level-index-2017-h1-report?utm_medium=socialmedia&utm_campaign=bli-lp-report
Informed decision-making
By utilizing the essential insights and data from Incenter, you’ll be confident in your decisions regarding security investments, resource allocation, and risk mitigation strategies while safeguarding your network and systems, further maturing your security posture.

Regulatory compliance
In today’s complex regulatory environment, organizations must adhere to a wide range of industry-specific and data protection regulations. Non-compliance penalties are severe and can exceed over $1,000,000 for every day compliance is neglected.5 Incenter assists in adhering to stringent cybersecurity guidelines and requirements of these compliance standards.
Learn how Incenter can assist your compliance
5 Baker McKenzie. (2022). What are the potential penalties / remedies for non-compliance with the key data privacy and security laws in the jurisdiction? https://resourcehub.bakermckenzie.com/en/resources/data-privacy-security/north-america/united-states/topics/penalties-for-noncompliance
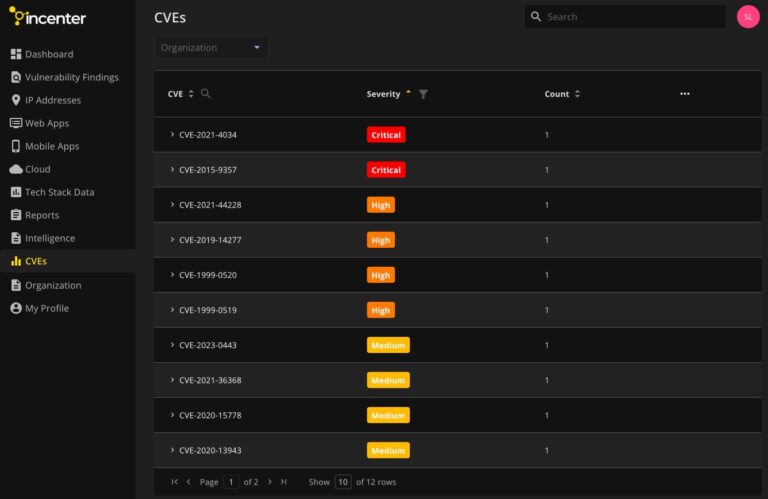
There are also many technical benefits to Incenter. Click to learn more about how Incenter can help you.
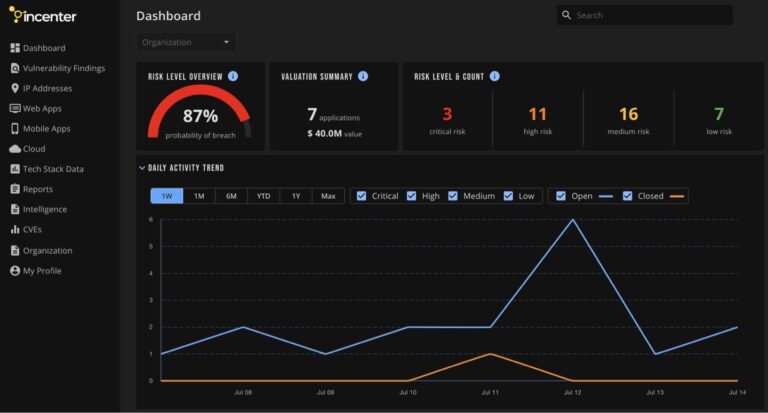
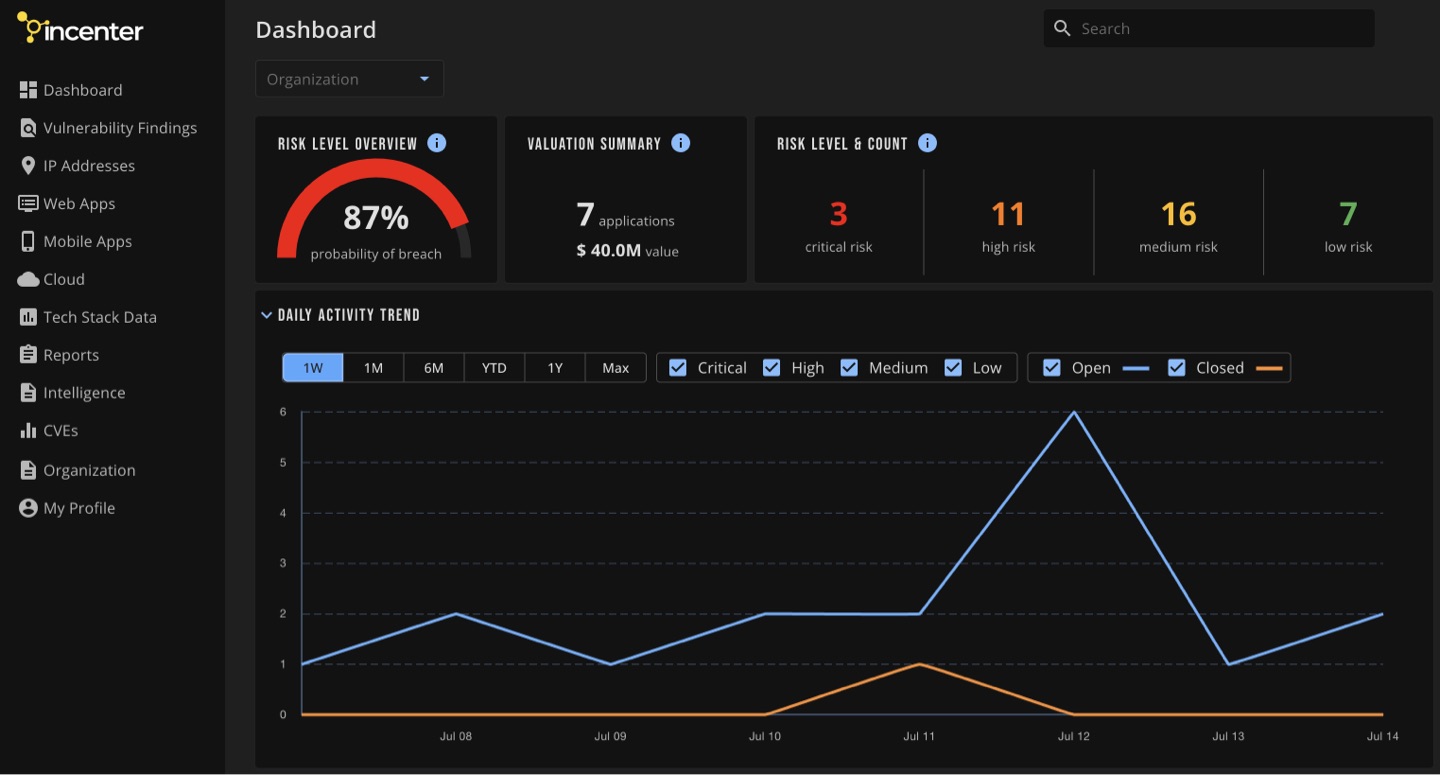
Incenter dashboard homepage overview
Incenter subscription tiers
We offer various subscription levels to suit your requirements. Meaning you never pay for anything you don’t need.
| Feature / Benefit | Essential | Business | Enterprise |
|---|---|---|---|
| Occamatic Automation Engine | |||
| Single Sign On Integration | |||
| Incenter Access for Unlimited Users | |||
| On Demand Reporting | |||
| Access to Client Success Team | |||
| Knowledge Base | |||
| Remediation Testing | |||
| Intelligence Briefings | |||
| Access to Consulting Team | |||
| Attacker Emulation | |||
| Monthly Program Review with Success Team | |||
| Extended Attack Emulation | |||
| Introductory Onboarding Call | |||
| Live Training Session | |||
| Bi-Annual Business Review |
Some of the industries we serve
Supporting you
A dedicated Incenter client success team is available to maximize your security ROI. The Incenter team provides technical and security-related support to ensure your organization’s security goals.
Partnership opportunities
We work with our partners to solve clients' problems to help them achieve their objectives